Guides
How to Encrypt OAuth 2.0 GitHub Credentials with Python
This guide will help you encrypt access tokens for GitHub login with OAuth 2.0. Clone this GitHub repo or fork this Replit to follow along.
Most apps to provide single sign-on to log in and sign up, and for good reason. Not only is it more convenient for users, it is also safer and more secure than asking users to login with passwords. That doesn’t mean its without its risks.
Using OAuth 2.0, integrations with third parties can give you full control over your customers' accounts with third-parties. The data that is transmitted, in the form of an access token or client secret, is considered sensitive data because if someone has access to that token, they could issue requests with it and gain access all the user information.
Encrypting OAuth access tokens is a quick and easy way to add a layer of security and prevent a potentially costly data breach. In this guide you will build an authentication flow using GitHub OAuth that encrypts the access token using Outbound Relay.
Once completed, you will see that you are logged in with GitHub, but your access token always remains encrypted. The working demo will look like the below, only with your GitHub details logged:
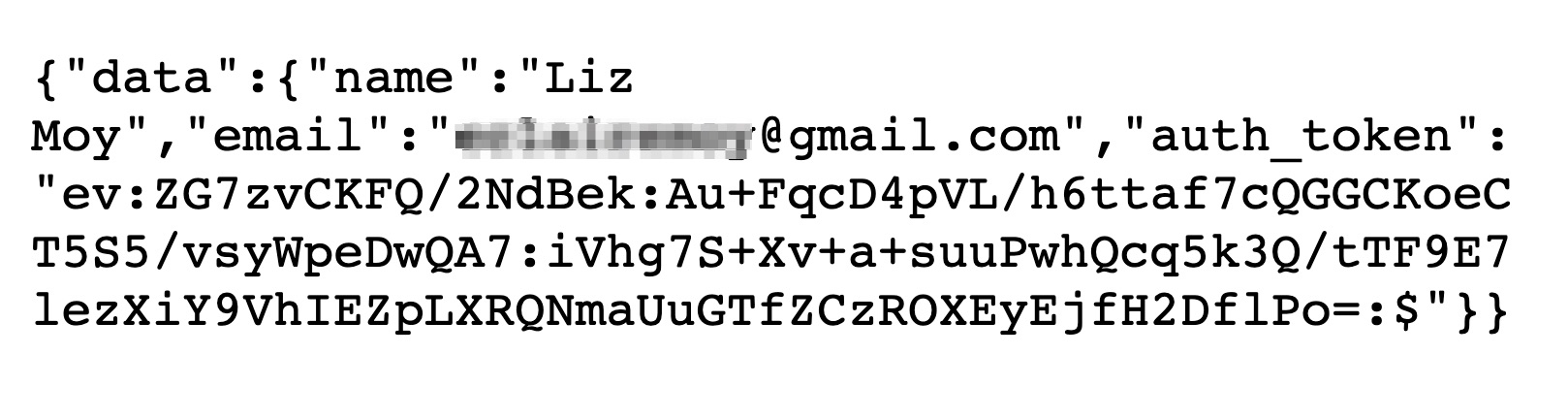
Prerequisites
- An Evervault Account (sign up for free here)
- A GitHub OAuth App (create one from your GitHub account)
- Python v3.6.0 or higher
Set up the project
Clone the working GitHub repo or fork the Replit.
In the main project directory, create and activate a virtual environment.
Next, install the required packages to the virtual environment.
pip3 install -r requirements.txt
Now you have all the libraries required to run the app.
Add your Evervault API Key
Create a new Evervault App. Then go the App Settings page. You will need to set your Evervault App ID and API Key as an environment variable.
A .env.example has been provided for you, so add in the credentials to the corresponding variables, then rename it to .env.
Create a GitHub OAuth app
Anyone with a GitHub account can create a GitHub OAuth app in just a few steps. While signed into your account, go to the Developer settings and click on OAuth Apps from the sidebar. Then click the New OAuth App button.
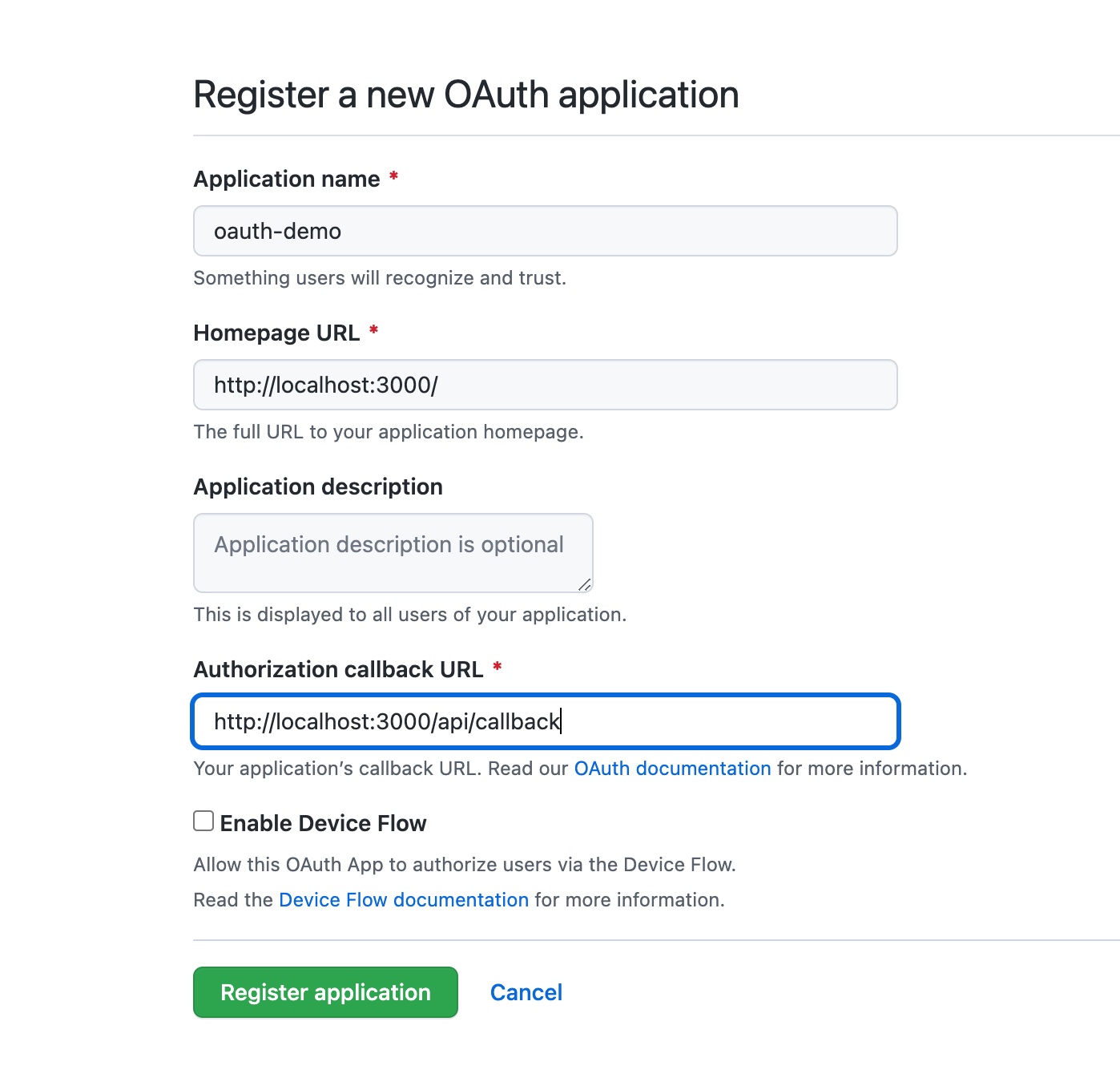
Fill in the details required including the name of your app, the homepage URL, and the Authorization callback URL.
If you are running the application using Replit, your endpoints will need to be from Replit rather than localhost. They should look like https://github-credentials-with-python.evervault.repl.co, with the format of https://<project-name>.<username>.repl.co/
Your Homepage URL should be your localhost.
http://localhost:5000/
The Authorization callback URL should be that link with /callback appended.
http://localhost:5000/callback
This maps to the callback function, which you will take a look at in the next step.
Click Register application, which will take your application settings dashboard. Similar to the previous step where you added Evervault environment variables, add the GitHub Client ID and GitHub Client Secret as variables in your .env.
You will need to re-authenticate with GitHub in order to generate and access the Client Secret. Be sure to save it immediately because you won’t be able to access it again.
Next, you can run the Flask app to access the callback handler from your server.
Run the Flask app
Now. you can run the server using the below command.
flask run
You can skip ahead to configuring Outbound Relay in the next section, or if you’d like to understand what’s going on in the Python app you can read this section which will explain the code.
In this code, you first initialize the SDK and enable Outbound Relay.
Next, you receive the code in from the request. You need to exchange it for an access_token by making a POST request with the code. The access_token is returned in the response as JSON and will be encrypted by default with response encryption. If you want to ensure that it remains encrypted, check the terminal, where the print statement will display the encrypted access_token.
The last step is to use the access_token to get the name and email of the GitHub user. It requires specifically defined headers per GitHub requirements. Then you take the response from the call to get the user data, and return it as a JSON object.
When enabled, Outbound Relay handles the access token encryption. No additional encryption calls are required within the code. Using relay is safer than using server-side encryption, because if you encrypt on the server then it will have access to the data in plaintext.
Lastly, configure the GitHub endpoints in Outbound Relay.
Configure Outbound Relay
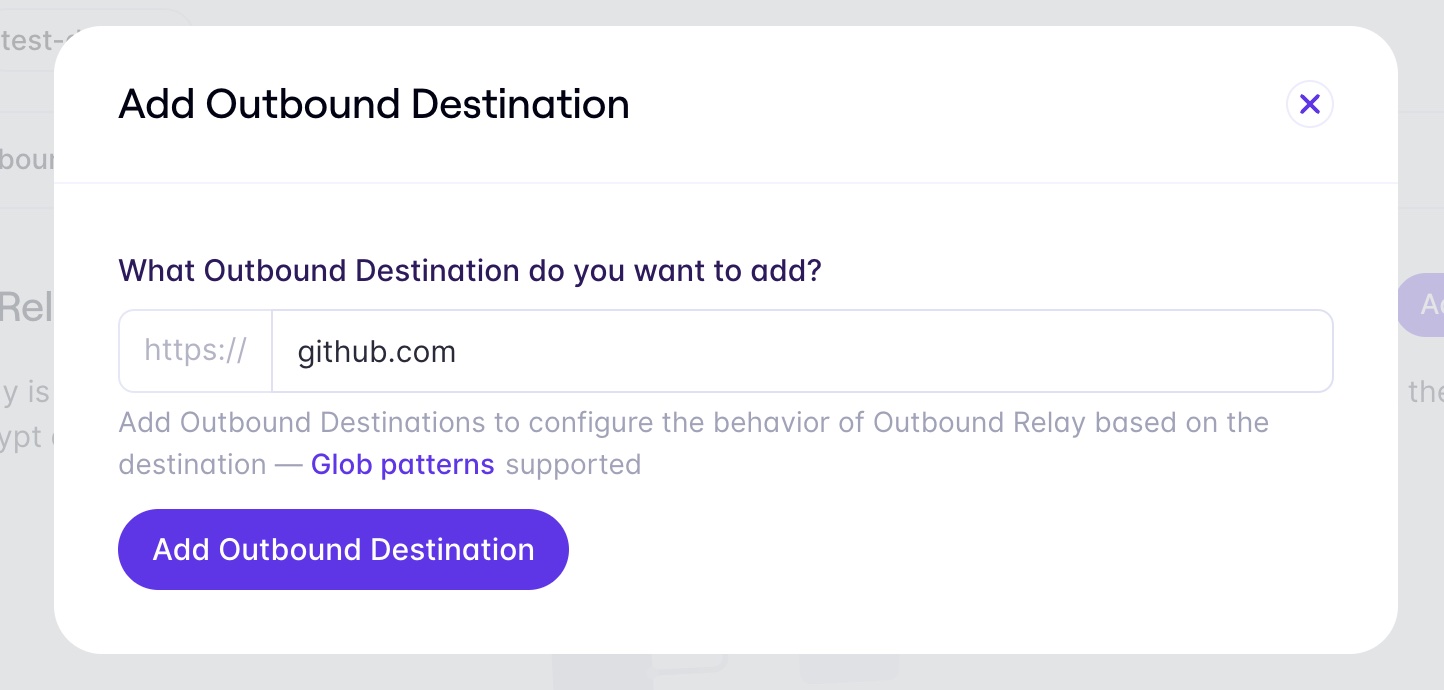
You will need to configure github.com as a destination to handle the initial request for the access_tokenas well as the request to get the user name and email.
Click Add Outbound Destination and add github.com.
Now in your Outbound Relay dashboard, add access_token as a field to encrypt under Response Encryption.
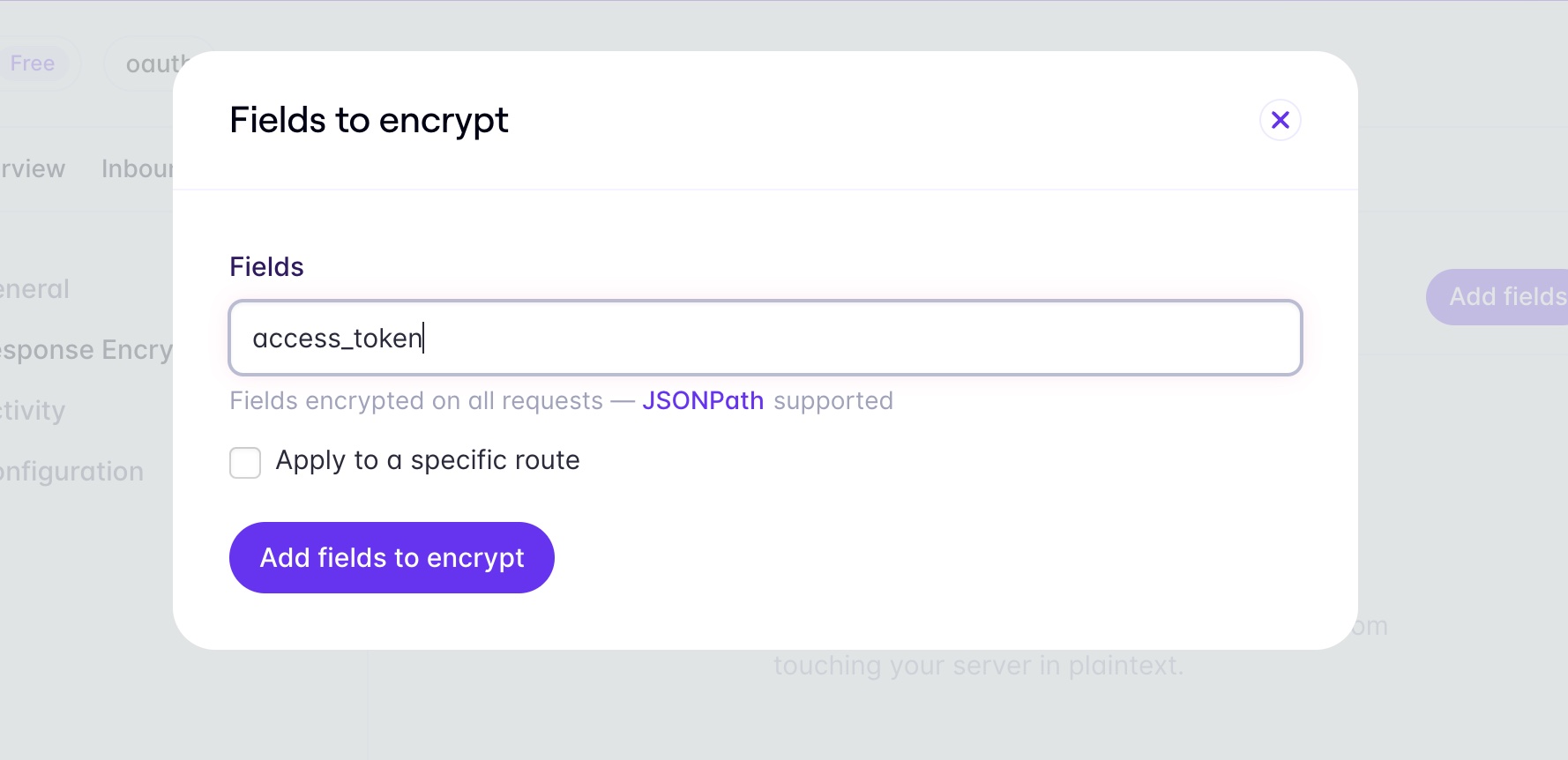
Repeat the process to add api.github.com as a destination.
Now your app should keep the access token encrypted when it comes back into your app, and will decrypt it instantly when it makes the second request for the user name and email.
Try it out!
Log in with GitHub
Now you can login with GitHub. In your browser, paste in https://github.com/login/oauth/authorize?scope=user:email&client_id=<YOUR_GITHUB_CLIENT_ID>
Make sure to replace the placeholder text in the URL with your Client ID.
It should take you to an authorization page that will look familiar if you’ve authenticated using GitHub before. Then you’ll be redirected to a page that logs the user data with access_token encrypted.
Conclusion
In this guide, you encrypted OAuth tokens using the Evervault Python SDK and Outbound Relay. If you ran into an issue or have any questions about this guide, feel free to raise them on GitHub. Encrypt all your sensitive data!